The advent of Web3 marks a transformative shift in the landscape of the Internet, representing a paradigmatic evolution from its predecessor, Web2. Web3 is not just an upgrade but a fundamental reimagining of the internet’s structure and functionality, encompassing decentralized technologies, blockchain, and a novel approach to user interactions.
Web2, characterized by centralized platforms, limited user control, and data silos, laid the groundwork for digital connectivity and collaboration. However, Web3 emerges as a decentralized ecosystem, driven by principles of trust, transparency, and user empowerment. This evolution signifies a departure from the hegemony of tech giants, offering a more inclusive and participatory online experience.
Web3 is distinguished by several key characteristics that define its nature and functionality. Decentralization is at its core, empowering users to have greater control over their data and digital identity. Blockchain technology plays a pivotal role, enabling secure and transparent transactions, while smart contracts facilitate trustless and automated interactions. Peer-to-peer networks and distributed storage systems further contribute to the decentralization ethos, reducing reliance on centralized servers.
What is the Importance of Security in Web3 Development?
Web3 development has ushered in a new era of decentralized and interconnected systems, transforming the way we interact with Web3 platforms. However, with this innovation comes an imperative need for robust security measures. The significance of security in Web3 development cannot be overstated, as it addresses the growing concerns and challenges that have emerged in this dynamic landscape.
Decentralization and Security
The fundamental principle of decentralization, a cornerstone of Web3, brings both promise and peril. While it fosters trustless transactions and reduces reliance on intermediaries, it introduces new security challenges.
Traditional centralized security models may not be sufficient in this decentralized paradigm. Web3 security demands a paradigm shift, emphasizing distributed consensus mechanisms, cryptographic techniques, and blockchain immutability to safeguard data and transactions.
Smart Contracts Vulnerabilities
Smart contracts, the self-executing code on blockchains, are integral to Web3 applications. However, their complexities and the immutable nature of blockchains make them susceptible to vulnerabilities.
Security in Web3 requires a meticulous approach to smart contract development, including rigorous testing, code audits, and adherence to best practices. Web3 security audits play a crucial role in identifying and mitigating vulnerabilities before deployment, ensuring the integrity of decentralized applications (DApps).
Identity and Privacy Risks
In the Web3 ecosystem, users have greater control over their digital identities. However, this empowerment comes with the risk of identity theft and privacy breaches. Securing user identities and sensitive information is paramount.
Web3 security solutions must integrate privacy-centric technologies, such as zero-knowledge proofs and decentralized identity frameworks, to mitigate these risks. Implementing a comprehensive Web3 Security Stack is essential to fortify the layers of defense against potential threats.
What are the Fundamentals of Web3 Security?
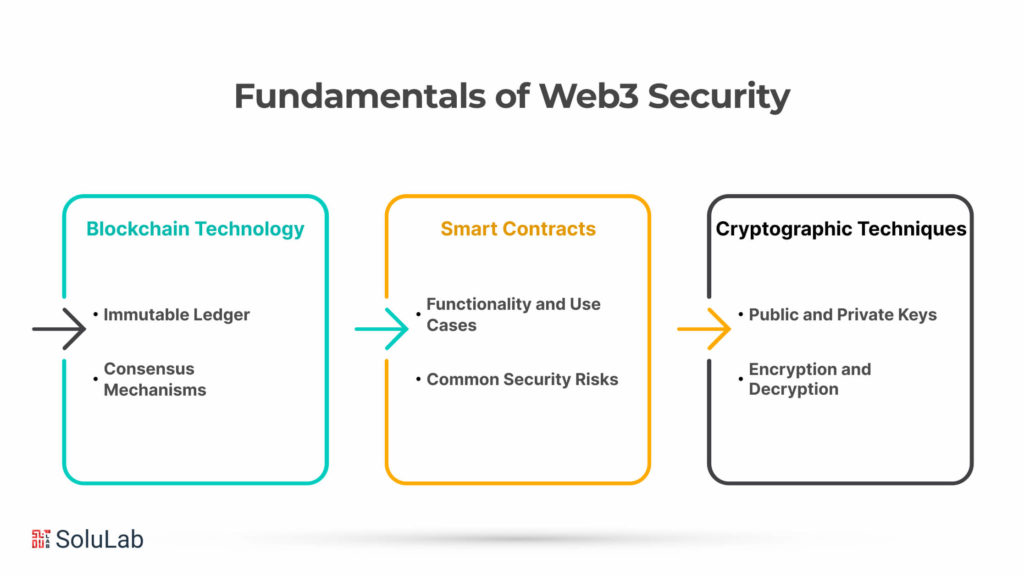
In the dynamic landscape of decentralized technologies, Web3 security emerges as a paramount concern, necessitating a comprehensive understanding of its foundational elements. This section delves into the core aspects of Web3 security, exploring the critical components that underpin its robustness.
A. Blockchain Technology
Blockchain technology forms the bedrock of Web3 security, introducing revolutionary concepts that redefine trust and transparency in digital transactions.
-
Immutable Ledger
At the heart of Web3 security lies the immutable ledger, a decentralized and tamper-resistant record of transactions. This characteristic ensures that once information is added to the blockchain platform, it becomes practically impossible to alter, enhancing data integrity and fostering a high level of security in Web3 environments.
-
Consensus Mechanisms
Consensus mechanisms play a pivotal role in maintaining the security and integrity of decentralized networks. Through protocols like Proof of Work (PoW) and Proof of Stake (PoS), blockchain systems ensure agreement among network participants, thwarting malicious activities and reinforcing the overall security in the realm of Web3.
B. Smart Contracts
Smart contracts, self-executing agreements with the terms of the contract directly written into code, are instrumental in Web3 ecosystems, revolutionizing the way transactions are conducted.
-
Functionality and Use Cases
Web3 security relies heavily on the innovative functionality and diverse use cases of smart contracts. These automated contracts enable trustless interactions, reducing the need for intermediaries and enhancing security in Web3 transactions, from financial agreements to supply chain management.
-
Common Security Risks
Despite their transformative potential, smart contracts are not immune to security risks. Vulnerabilities such as code bugs, reentrancy attacks, and Oracle manipulations pose challenges to Web3 security. Conducting a Web3 security audit becomes imperative to identify and rectify these issues, ensuring the robustness of decentralized applications.
C. Cryptographic Techniques
The implementation of cryptographic techniques is a cornerstone in fortifying Web3 security, providing the encryption and decryption mechanisms necessary for safeguarding sensitive information.
-
Public and Private Keys
In the Web3 security landscape, the use of public and private keys is fundamental to user authentication and data protection. Public keys act as addresses, while private keys are secret credentials that grant access. The asymmetric nature of this cryptographic approach bolsters security in Web3 environments.
-
Encryption and Decryption
Secure communication and data integrity are upheld through encryption and decryption processes. Web3 security relies on advanced cryptographic algorithms to encode information during transmission and decode it only for authorized recipients, creating a shield against unauthorized access.
What are the Components of Web3 Security Stack?
A. Decentralized Identity Management
-
Self-Sovereign Identity (SSI)
In the realm of Web3 security, Self-Sovereign Identity (SSI) plays a pivotal role. It empowers individuals with control over their own identity without the need for intermediaries. SSI ensures that users have secure and private ownership of their digital identities, reducing the risk of identity-related fraud and enhancing overall security in the web3 environment.
-
Decentralized Identifiers (DIDs)
DIDs are fundamental to decentralized identity systems. They provide a mechanism for creating globally unique identifiers, enhancing security by eliminating reliance on central authorities. Incorporating DIDs in the DeFi in web3 era infrastructure ensures that entities can be uniquely identified and authenticated in a decentralized and secure manner.
B. Secure Communication Protocols
-
Interledger Protocol (ILP)
As an integral part of the web3 security landscape, ILP facilitates secure and efficient transactions across different ledgers. It ensures interoperability between various blockchain networks, enhancing the overall security and efficiency of decentralized transactions. ILP’s role is critical in achieving a seamless and secure flow of information in the web3 environment.
-
Whisper Protocol
Whisper Protocol is designed for secure communication within decentralized applications. Its emphasis on privacy and confidentiality aligns with the core principles of web3 security. By enabling private and encrypted messaging, the Whisper Protocol adds a layer of protection to communication channels, safeguarding sensitive information in the decentralized ecosystem.
C. Consensus Mechanisms
-
Proof of Work (PoW)
PoW, a well-known consensus mechanism, ensures the security of blockchain networks by requiring participants to solve complex mathematical problems. Its inclusion in the web3 security stack ensures the integrity of transactions and the overall network, providing a robust defense against malicious activities.
-
Proof of Stake (PoS)
PoS introduces an alternative consensus mechanism, relying on validators who hold a stake in the network. This approach enhances web3 security by reducing the environmental impact associated with PoW and promoting a more energy-efficient and sustainable decentralized ecosystem.
What are the Tools and Frameworks for Web3 Security?
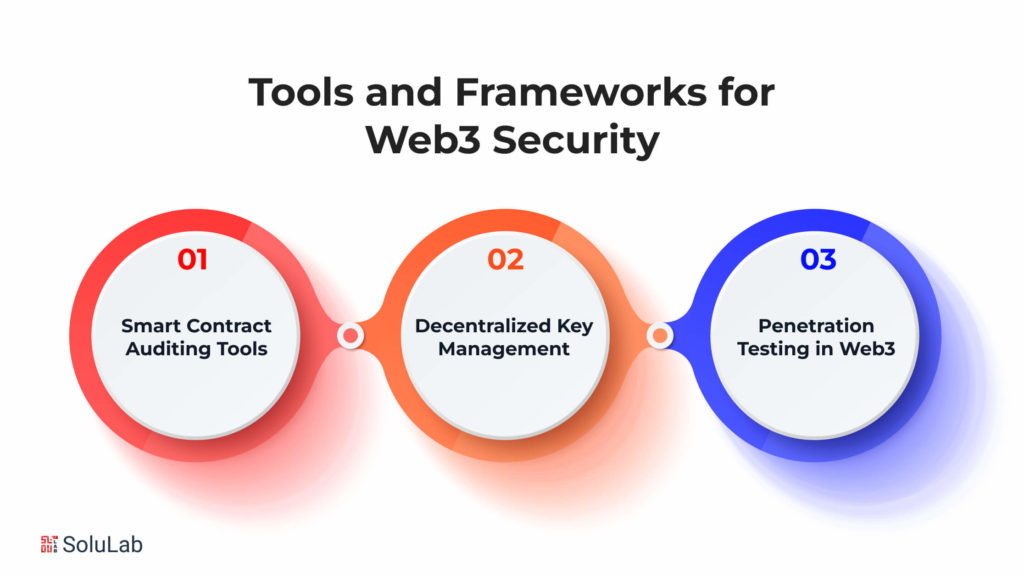
In the rapidly evolving landscape of Web3, ensuring robust security measures is paramount to safeguard decentralized applications (dApps) and smart contracts. The Web3 Security Stack comprises various tools and frameworks designed to fortify the decentralized ecosystem. Here’s a comprehensive exploration of key elements:
A. Smart Contract Auditing Tools
-
MythX
MythX stands at the forefront of smart contract security auditing. Leveraging advanced analysis techniques, it meticulously scans smart contracts for vulnerabilities. This tool is indispensable for developers seeking to enhance the security posture of their Web3 applications. MythX contributes significantly to proactively identifying and eliminating potential threats in the web3 security landscape.
-
Securify
Securify is another robust tool tailored for smart contract auditing. Recognized for its precision in detecting vulnerabilities, it employs formal verification methods to ensure the reliability and security of smart contracts within the Web3 domain. Securify plays a pivotal role in fortifying code against potential exploits, fostering a resilient foundation for web3 security audit processes.
B. Decentralized Key Management
-
Key Management Service (KMS)
Within the Web3 Security Stack, KMS emerges as a key enabler for decentralized key management. This service facilitates secure key storage, ensuring that cryptographic keys vital for the integrity of Web3 transactions are safeguarded against unauthorized access. KMS forms an integral part of the broader security infrastructure, enhancing the overall security posture in the realm of web3 security.
-
Hardware Security Modules (HSMs)
HSMs provide an additional layer of security by physically securing cryptographic keys. These modules safeguard against both logical and physical attacks, making them a cornerstone in decentralized key management for Web3 applications. Integrating HSMs into the infrastructure enhances the robustness of web3 security audit mechanisms.
C. Penetration Testing in Web3
-
Challenges and Approaches
Penetration testing in the context of Web3 introduces unique challenges due to the decentralized nature of blockchain networks. Addressing issues such as consensus algorithm vulnerabilities and smart contract exploits requires specialized approaches. Robust penetration testing methodologies are crucial for identifying and mitigating potential risks, contributing to a comprehensive web3 security strategy.
-
Security Auditing Platforms
Security auditing platforms play a vital role in evaluating the overall security posture of Web3 applications. These platforms combine automated tools and manual assessments to identify vulnerabilities comprehensively. Their integration into the Web3 Security Stack reinforces the reliability and trustworthiness of decentralized ecosystems.
What are the Key Components of Secure Coding?
In the rapidly evolving landscape of Web3, ensuring robust security practices is paramount to safeguarding decentralized systems. Implementing the best practices for Web3 security development requires a comprehensive approach, encompassing secure coding practices, continuous monitoring, and incident response strategies.
A. Secure Coding Practices
-
Code Reviews
Conducting thorough code reviews is a cornerstone of Web3 security. Regularly scrutinizing code by multiple developers helps identify vulnerabilities and ensures compliance with established security standards. The emphasis should be on scrutinizing smart contracts and decentralized applications (DApps) to mitigate potential exploits.
-
Static Analysis Tools
Leveraging static analysis tools is instrumental in identifying security loopholes in the early stages of development. Tools like MythX and Slither can analyze smart contract code for vulnerabilities, aiding developers in proactively addressing issues related to Web3 security.
B. Continuous Monitoring and Incident Response
-
Real-time Monitoring Solutions
Web3 security demands real-time monitoring to detect and respond swiftly to potential threats. Utilizing solutions such as blockchain explorers and network analyzers helps in tracking transactions, identifying anomalies, and promptly addressing security incidents. Continuous monitoring ensures the integrity and security of decentralized networks.
-
Incident Response Plans
Develop comprehensive incident response plans specific to Web3 environments. These plans should outline procedures for detecting, reporting, and responding to security incidents. Collaborate with the broader community to establish a unified response strategy. Regularly test and update these plans to adapt to evolving threats in the dynamic Web3 landscape.
What are the Future Trends in Web3 Security?
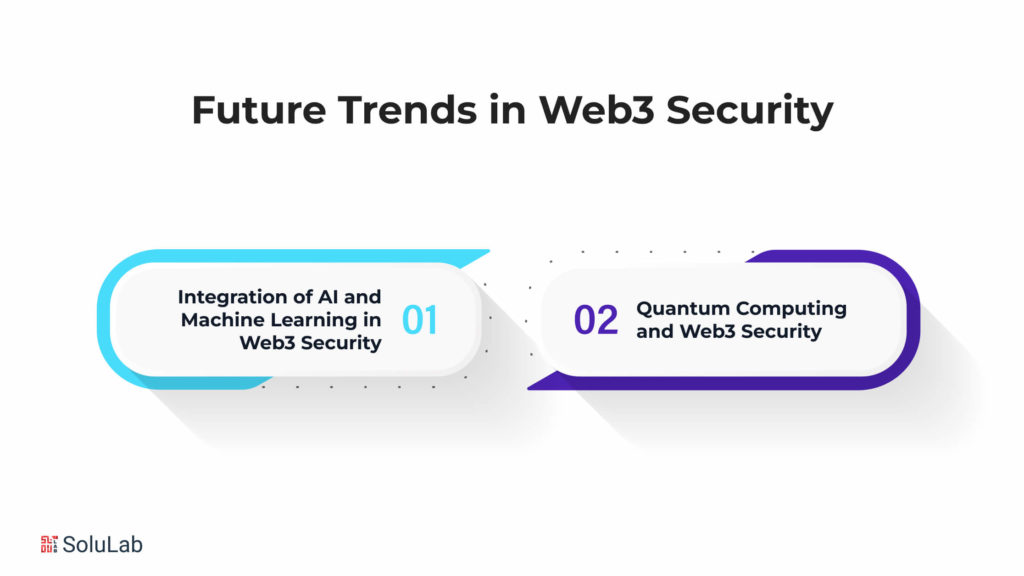
In the ever-evolving landscape of the internet, the emergence of Web3 brings forth new challenges and opportunities in the realm of cybersecurity. As we navigate the complex terrain of decentralized networks, the future trends in Web3 security are poised to revolutionize how we safeguard digital assets and information. Here, we delve into two key aspects: the data integration of AI and machine learning, and the impact of quantum computing on Web3 security.
A. Integration of AI and Machine Learning in Web3 Security
-
Predictive Security Measures
In the dynamic environment of Web3, predictive security measures powered by AI and machine learning algorithms play a pivotal role. Traditional reactive approaches are being complemented by proactive strategies that anticipate potential threats.
By analyzing patterns, user behaviors, and transactional data, these intelligent systems can predict and prevent security breaches before they occur. This shift from a reactionary to a preventative stance enhances the overall security posture in the Web3 landscape.
-
Anomaly Detection
Web3 security necessitates a heightened focus on anomaly detection mechanisms. AI and machine learning models excel in identifying deviations from normal behavior, enabling the rapid detection of suspicious activities.
Whether detecting unauthorized access attempts or flagging irregularities in smart contract executions, anomaly detection adds a crucial layer of defense to Web3 ecosystems.
B. Quantum Computing and Web3 Security
-
Threats and Countermeasures
The advent of quantum computing poses unprecedented challenges to classical cryptographic methods, potentially compromising the security foundations of Web3. As quantum computers advance, they could break widely used encryption protocols, jeopardizing the confidentiality and integrity of data.
To counter this, Web3 security must embrace quantum-resistant algorithms and cryptographic techniques to ensure the continued protection of sensitive information.
-
Post-Quantum Cryptography
Recognizing the imminent threat of quantum computing, the integration of post-quantum cryptography becomes imperative for Web3 security.
This entails adopting cryptographic algorithms resilient to quantum attacks, safeguarding sensitive transactions and communications in a quantum-powered future. The proactive implementation of post-quantum cryptography serves as a crucial defense strategy against potential quantum threats.
What are the Regulatory Landscape and Compliance in Web3?
The regulatory landscape surrounding Web3 technologies is continually evolving, driven by global regulatory trends that aim to address the unique challenges posed by decentralized systems. In this section, we explore the shifting legal frameworks and compliance challenges within the Web3 space, emphasizing the critical aspect of security through concepts such as web3 security, security in web3, web3 security audit, and the Web3 Security Stack.
A. Evolving Legal Framework
-
Global Regulatory Trends
In the dynamic realm of Web3 technologies, global regulatory trends play a pivotal role in shaping the legal framework. Governments and regulatory bodies worldwide are increasingly recognizing the impact of decentralized technologies on traditional systems.
As the Web3 landscape expands, regulators are responding with a mix of caution and innovation, attempting to strike a balance between fostering technological advancements and safeguarding against potential risks.
Key considerations in global regulatory trends include:
- Recognition of decentralized finance (DeFi) and blockchain-based systems.
- Efforts to establish clear definitions for cryptocurrencies and tokenized assets.
- Formulation of guidelines for Initial Coin Offerings (ICOs) and Security Token Offerings (STOs).
- Cross-border collaboration to address jurisdictional challenges in the decentralized space.
- Compliance Challenges in Web3:
- Navigating the Web3 landscape presents unique compliance challenges, primarily due to its decentralized and borderless nature. Compliance efforts must adapt to the decentralized ethos while addressing concerns related to financial regulations, data protection, and consumer rights.
Organizations operating within the Web3 ecosystem encounter the following compliance challenges
- Ambiguity in regulatory classifications for decentralized entities.
- Ensuring adherence to anti-money laundering (AML) and know-your-customer (KYC) regulations.
- Handling cross-border legal complexities arising from decentralized applications and global user participation.
- Establishing frameworks for transparent governance and accountability in decentralized autonomous organizations (DAOs).
B. Web3 Security Focus
Web3 Security is a critical aspect that underpins the successful integration of decentralized technologies into mainstream use. Various security measures are essential to fortify the Web3 ecosystem and ensure the protection of assets, data, and user privacy. Incorporating keywords such as web3 security, security in web3, web3 security audit, and the Web3 Security Stack becomes paramount in this context.
-
Web3 Security Audit
Conducting regular security audits is imperative to identify vulnerabilities within decentralized systems. A comprehensive web3 security audit involves:
- Smart contract audits to ensure code integrity and protection against exploits.
- Network security assessments to identify potential attack vectors and vulnerabilities.
- Verification of cryptographic protocols and consensus mechanisms.
- Evaluation of governance mechanisms to prevent malicious activities within DAOs.
- Web3 Security Stack:
- The Web3 Security Stack comprises a layered approach to fortify the decentralized ecosystem against threats.
Key components include
- Secure smart contract development practices.
- Robust consensus algorithms ensure network integrity.
- Encryption and privacy-focused protocols safeguarding user data.
- Continuous monitoring and threat detection mechanisms.
Conclusion
In conclusion, SoluLab emerges as a pioneering force in the realm of Web3 security, providing an invaluable resource for developers navigating the complex landscape of decentralized technologies. This comprehensive guide not only elucidates the intricacies of the Web3 Security Stack but also underscores SoluLab’s commitment to empowering developers in safeguarding their decentralized applications.
By delving into the nuances of Web3 security, SoluLab’s guide serves as a beacon for developers seeking a profound understanding of the evolving threat landscape. The company’s emphasis on proactive measures and best practices demonstrates a forward-thinking approach to ensuring the integrity and resilience of Web3 applications.
In the competitive landscape of Web3 development, SoluLab stands out not only as a reliable source of knowledge but also as a premier web3 development company that bridges the gap between theoretical insights and practical implementation. Aspiring developers looking to bolster their projects can confidently turn to SoluLab’s expertise and, where necessary, hire web3 developers with the assurance of gaining access to a wealth of knowledge and experience.
SoluLab’s commitment to advancing Web3 security extends beyond the confines of this guide, as the company continues to contribute to the development of secure and robust decentralized ecosystems. In essence, this guide not only equips developers with the tools to navigate the challenges of Web3 security but also positions SoluLab as a leading force in the ever-evolving landscape of decentralized technologies.
FAQs
1. What is Web3 Security Stack, and why is it essential for developers?
Web3 Security Stack is a comprehensive set of protocols and practices designed to ensure the security of decentralized applications (dApps) in the Web3 ecosystem. Developers must implement these measures to safeguard against potential vulnerabilities and threats.
2. How does Web3 Security differ from traditional web security?
Web3 Security focuses on securing decentralized applications and blockchain technologies, considering the unique challenges and risks associated with distributed systems. Traditional web security measures may need to be revised in the context of decentralized networks.
3. Why should developers prioritize security in Web3 development?
Security is paramount in Web3 development to protect sensitive data, and financial transactions, and ensure the integrity of decentralized systems. A strong security foundation also enhances user trust and confidence in dApps.
4. What are the key components of the Web3 Security Stack?
The Web3 Security Stack includes elements like smart contracts in Web3 security, decentralized identity management, secure key management, and secure decentralized data storage. Each component addresses specific aspects of security in Web3 development.
5. How can a Web3 Security Audit benefit developers?
A Web3 Security Audit is a thorough examination of a decentralized application’s codebase, smart contracts, and overall architecture to identify and mitigate security vulnerabilities. It helps developers preemptively address issues and enhance the overall security posture.
6. What role do Web3 developers play in ensuring security?
Web3 developers are instrumental in implementing secure coding practices, conducting regular security audits, and staying informed about the latest security threats. Their expertise is vital in building resilient and secure decentralized applications.