
2025 was a major year for crypto. Bitcoin neared $110K, DeFi recovered, and new exchanges finally grew, but the risks grew even faster. The $1.5B Bybit hack shook the industry, and by Q3 2025, total losses hit $2.55B across 344 incidents, with hot-wallet attacks driving most of the damage.
Going into 2026, the market is rising, but so are attackers. Immunefi reported $1.64B lost in Q1, the worst quarter ever, and the year may cross $4B. Running an exchange today means protecting real user money, not just shipping features. Most big breaches happened because teams skipped key checks or treated audits lightly.
This guide explains how audits work in 2026 and what founders can apply immediately to secure their platforms.
Key Takeaways
- In the first half of 2025, $2.37B was stolen, up 66% from 2024. Most attacks hit hot wallets (62%) and exploited poor access controls (75%).
- The solution is MPC and Multi-Sig custody. Protocol-agnostic and keyless reconstruction, these setups are replacing single-sig for scalability and safety.
- Experts now recommend keeping 95–98% of funds in cold storage, leaving just 2–5% hot. Even ByBit, with $1.5B on hand, lost 69% of its H1 exposure due to mismanaged hot wallets.
- Continuous monitoring and retesting beat annual audits hands down. Over half of new DeFi projects were hacked in year one, losing $540M, simply because gaps went unnoticed.
Why Exchange Security Matters More Than Ever in 2026?
If you’re building a crypto exchange in 2026, one thing that decides growth is trust. And trust today comes from strong, modern, and tested security. Only 4.2% of stolen funds are ever recovered because hackers now use mixers, cross-chain swaps, and fast-laundering tools.
But smart exchanges win by doing the opposite. Platforms like Kraken keep 95% of assets in cold storage and haven’t faced a major breach since 2011. That’s why institutions in 2025 preferred exchanges with strong custody, clear audits, and transparent security systems.
At the same time, threats in 2026 are rising:
- AI-driven attacks grew 40%.
- Targets now include supply-chain tools, APIs, admin panels, and custody partners.
- India, the EU, and the US now require SOC 2, ISO 27001, VASP, and other mandatory audits.
The space is getting tougher, but also clearer. When teams treat security as a core product feature, they build centralized exchanges that users trust, investors respect, and regulators approve.
How to Make Your Crypto Exchange Hack-Proof in 2026?
When a crypto exchange is built for 2026, the foundation must match the speed, scale, and security expectations of the modern trading ecosystem. A high-performance white label exchange is designed around protection, uptime, performance, and compliance from day one. The following approach ensures the product stays secure, stable, and resistant to modern attack surfaces.
1. Threat Modeling That Covers Real Attack Paths
A complete threat model is created before crypto exchange development begins. It outlines every possible attack direction, such as:
- API abuse and request manipulation
- Compromised support devices
- Attempts to reach the matching engine
- Third-party custody failures
- Withdrawal bypass strategies
This becomes the core security blueprint that drives architecture and implementation decisions.
2. Institutional-Grade Custody Infrastructure
Most crypto losses happen because someone gets access to a private key. In 2024, that number was 43.8% of all stolen crypto. So we build custody like a fortress:
- HSM- or MPC-backed key management, so keys never appear in raw form
- Multi-signature workflows like 3-of-5 or 4-of-6 with separate roles
- Time-locked withdrawal queues
- Third-party custodians are treated as untrusted, with strict API rules
This is how modern, secure crypto exchanges stay safe with no single point of failure.
Read Also: Custodial vs. Non-Custodial Wallets
3. Multi-Layer Defense Stack From Day Zero
A modern exchange uses a layered defense model inspired by top global exchanges. More than 95% of assets remain in cold storage, while hot wallets are protected through:
- Require multi-signature approvals for all administrative actions to prevent single-point failures.
- Implement 4-eyes verification for high-value transactions to ensure extra oversight.
- Use segregated signing devices to restrict access and reduce the risk of compromise.
- Leverage AI-based anomaly detection to spot unusual withdrawals and suspicious activity in real time.
This year alone, these systems helped three of our clients avoid exploits worth $3M in possible losses.
4. Human-Layer Security to Prevent Phishing & Insider Risks
Human error remains one of the biggest risk areas. Strong exchanges include:
- Regular phishing simulations
- Secure workflow training
- Quarterly attack response drills
- Enterprise endpoint protection (EDR)
- Clear internal security playbooks
This reduces operational vulnerabilities dramatically.
5. Continuous Security Testing Built Into the Product
Security is treated as an ongoing process, not a one-time setup. The exchange lifecycle includes:
- Quarterly penetration tests
- Automated CI/CD vulnerability scans
- Red-team exercises
- Incident-response testing
This ensures stability even as the platform evolves.
Important Security Layers Your Crypto Exchange Should Never Skip
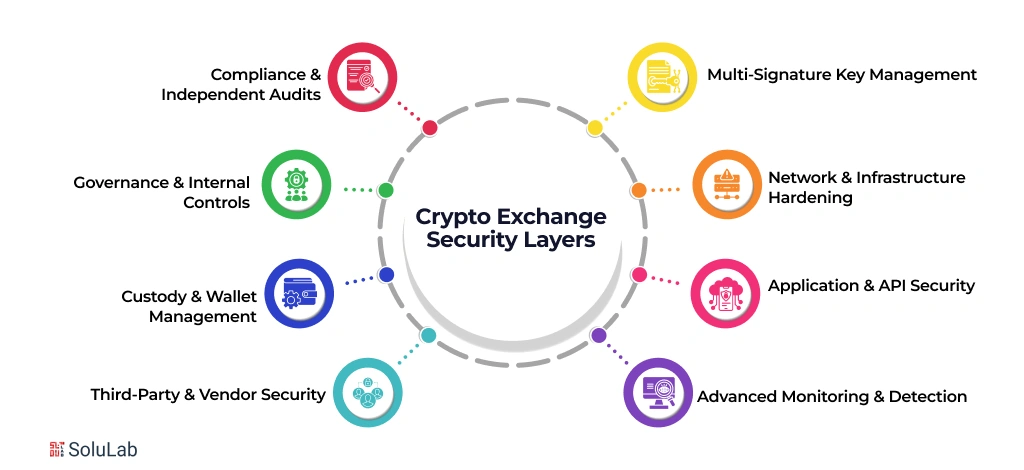
Building a decentralized crypto exchange in 2026 is about stacking strong, modern defenses while accounting for crypto taxes. Skip a single layer, and the entire system becomes vulnerable. Here is how we build exchanges that match 2025–2026 security standards:
1. Multi-Signature Key Management
Most crypto breaches still come from private key exposure. In 2024, 43.8% of all stolen crypto happened because one key was compromised. Modern exchanges avoid this with distributed, hardware-backed key systems.
- MPC wallets where key shares never appear together
- HSM-secured storage with institutional encryption
- Threshold signatures for all withdrawals
- Automated key rotation triggered by anomalies or role changes
This setup prevented a major exchange from losing 98% of assets during a 2024 hot wallet breach, limiting multi-sig losses to just 2%.
2. Network & Infrastructure Hardening
Infrastructure is the second-most targeted layer. Attackers exploit weak servers, exposed APIs, or misconfigured access. Strong hardening stops interception, lateral movement, and data manipulation.
- Air-gapped cold wallets with no internet path
- Bastion hosts with enforced MFA for all admin access
- Zero-trust verification for every request and service
- Micro-segmentation so KYC, trading, and wallets never touch
This eliminates the lateral movement patterns seen in most 2025 breaches, where attackers moved from a weak microservice to the core engine.
3. Application & API Security
Logic bugs, API abuse, and automated attacks remain the top vectors for draining hot wallets. Over 70% of exchange exploits begin at the app/API level.
- Full API penetration testing for logic abuse
- Rate-limiting and IP velocity checks to stop bots
- Short-lived sessions, device fingerprinting, and forced re-auth
- Withdrawal whitelist to block unknown addresses
This is how modern platforms block brute-force, credential stuffing, and API manipulation before funds are at risk.
4. Advanced Monitoring & Detection
No exchange is 100% immune. What matters is spotting anomalies fast. In Q3 2025, fast-response systems recovered up to 42% of funds in high-profile attacks.
- Anomaly alerts for strange withdrawals, login patterns, and trading behavior
- Continuous on-chain monitoring for bridge or smart contract risk
- Automatic circuit breakers pause withdrawals when thresholds trip
- 24/7 SOC running incident playbooks
Real-time intelligence turns potential multi-million-dollar losses into controllable events.
5. Third-Party & Vendor Security
Recent attacks show that vendors like custody partners, analytics tools, and KYC providers are now the easiest entry points. Attackers bypass exchanges by breaching integrations.
- Strict vendor security audits before integration
- Least-privilege API keys with isolation
- Mandatory rotation of all third-party credentials
- Breach-notification SLAs and continuous vendor monitoring
This protects your exchange even if a vendor gets compromised, turning weak links into controlled, isolated components.
6. Custody & Wallet Management
Hot wallets remain the biggest financial risk. In 2025, 62% of all exchange losses came from poorly managed hot wallets. Proper custody management protects core assets.
- Less than 5% of assets stay in hot wallets
- Cold wallets are stored offline and geographically distributed
- Multi-layer encryption with tamper-evident storage
- Automated rules for moving liquidity safely
This ensures day-to-day operations stay smooth while 95%+ of user funds remain beyond attacker reach.
7. Governance & Internal Controls
Insider risk, misconfigurations, and uncontrolled access are behind many invisible failures. Proper governance keeps every internal action accountable.
- Role-based access across every system
- Mandatory credential rotation schedules
- Separation of duties between code, UI, wallets, and trading
- Immutable audit logs are retained indefinitely
This structure prevents insider mistakes and ensures every sensitive action is logged and verifiable.
8. Compliance & Independent Audits
Security is technical proof; compliance is external validation. Exchanges that follow global frameworks earn trust faster and scale more easily.
- SOC 2 Type II aligned processes
- ISO 27001 security roadmap
- FATF and VASP compliance for international operations
- Regular internal and third-party audits double as security checks
Compliance transforms your security stack into measurable, externally certified trust.
Smart Add-Ons to Stop Exploits Before They Happen
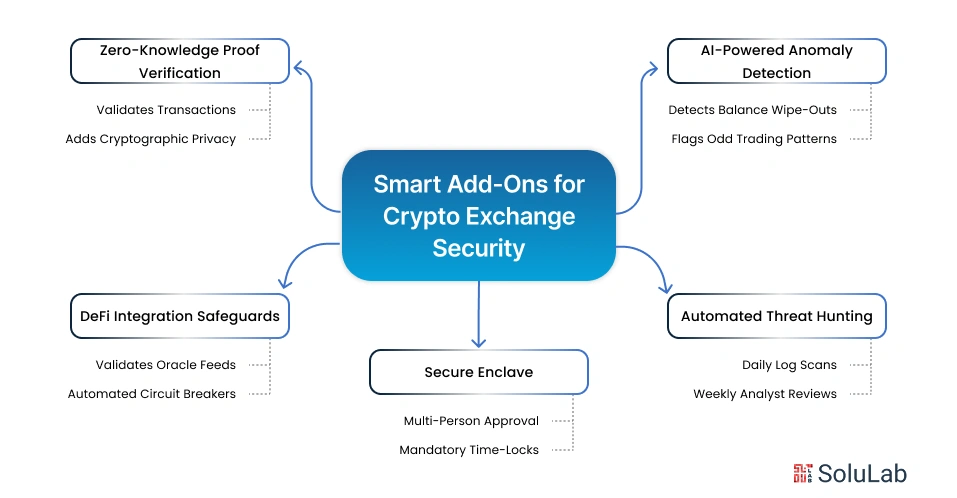
Modern attackers move fast. These add-ons detect threats before they touch your core systems. They give your exchange a proactive, institutional-grade edge, turning your platform into a secure crypto exchange built for 2026 threats, not 2020 best practices.
1. AI-Powered Anomaly Detection
Attackers evolve faster than rule-based systems. AI integration fixes that by tracking real user patterns and flagging anything, even unknown threats that drift from normal behavior.
- Detects sudden balance wipe-outs, new-address withdrawals, cross-country logins
- Flags odd trading patterns, API misuse, and scripted actions
- Reduces false positives by 70% while catching 95% of real threats
- Inspired by how models like HeyElsa AI read behavioral fingerprints
This gives your security team cleaner alerts, less noise, and faster reactions against unseen exploits.
2. Automated Threat Hunting
Continuous threat hunting finds risks before attackers weaponize them.
- Daily scans for Indicators of Compromise in logs
- Weekly human analyst review for patterns AI might miss
- Monthly threat-intel updates based on your exchange type
This layer catches quiet attackers hiding in networks long before they attempt a theft.
3. Secure Enclave for High-Value Withdrawals
Large withdrawals might be risky. A secure enclave adds friction only at the moments that matter most.
- Multi-person approval with video verification
- Threshold signatures from multiple trusted devices
- Mandatory time-lock for high-value withdrawals
- Cryptographic proofs before funds are released
Institutional clients expect this as it prevents insider abuse and adds a compliant, high-trust approval layer.
4. DeFi Integration Safeguards
If your exchange connects to DeFi, you inherit DeFi’s risks. We add smart safeguards to protect liquidity and users.
- Validate Oracle feeds to stop price manipulation
- Automated circuit breakers when partner protocols behave abnormally
- Token listing audits to block malicious or spoofed tokens
This is how DeFi exchanges stay safe from oracle attacks, flash loan manipulation, and malicious token injections.
5. Zero-Knowledge Proof (ZK) Verification
Zero-Knowledge Proof gives privacy and safety. It verifies actions without exposing user data.
- Validate transactions without revealing sensitive info
- Add strong cryptographic privacy guarantees
- Future-proof your exchange for global data protection standards
This positions your platform for both regulatory expectations and next-gen privacy requirements.
Conclusion
Building a crypto exchange in 2026 is a huge opportunity, but the risks are just as real. The $2B+ hacks from 2024–2025 prove how quickly weak architecture, poor custody design, or missing incident-response plans can destroy a product. Security cannot be a last-minute task; it must guide your architecture, vendors, and operations from day one.
Exchanges that invest in multi-layer security, cold storage, RBAC, and continuous security audits become the platforms users and institutions trust. The winners in 2026 will be the ones who prove resilience and transparency, not speed.
As a cryptocurrency exchange development agency, we’ve seen great products fail because founders treated security as a checkbox. Don’t make that mistake. With strong audits and smarter security layers, the breaches of past years are avoidable. If you’re building or scaling an exchange, now is the time to secure your roadmap, and we’re here to help you build a platform that users trust and stay with.
FAQs
1. How much does a comprehensive security audit cost?
A full crypto exchange audit usually ranges from $20,000 to $200,000, depending on your platform’s size and complexity. It may seem like a lot, but considering that the average hack in 2024 cost $15.7 million, it’s an investment that protects your funds, brand, and trust with users and institutions.
2. How often should we audit our exchange?
At least once a year and every time you make major changes. Top exchanges also adopt continuous testing with quarterly penetration scans and ongoing threat hunting, because most vulnerabilities appear after updates or new features.
3. Can a security audit guarantee we won’t be hacked?
No audit can promise 100% safety. But a thorough audit makes your platform harder and costlier to attack. Combined with multi-layer security and continuous monitoring, it has prevented millions in potential losses for many exchanges.
4. What’s the difference between a smart contract audit and a full exchange audit?
A smart contract audit only checks on-chain code. A full exchange audit covers your infrastructure, backend, trading engine, apps, APIs, wallets, custody, and admin tools. Since most centralized exchange hacks stem from infrastructure or custody failures, full audits are far more critical.
5. Do we really need multi-signature wallets?
Absolutely. Single-key wallets are a single point of failure. Multi-sig setups ensure that no one person or device can move funds alone, protecting against insider threats, social engineering, and vendor-side breaches.
6. How long does a full exchange security audit take?
Usually 4–6 weeks. This includes testing, reporting, fixing issues, and retesting. Rushing the process can leave serious blind spots.
7. What certifications should we aim for?
Start with SOC 2 Type II and ISO 27001 for general security assurance. If you operate as a VASP, follow the FATF Travel Rule and local licensing laws. These certifications help build trust with institutions and banking partners.







