The blockchain verification feature (of transactions) is that there is security, permanent records, irreversible, and maintained as a public ledger. One of the greatest features is that they have zero interference from any third party. All these characteristics have made blockchain so readily adaptable.
How can We Achieve Blockchain Verification?
Blockchains constitute code blocks linked together and depend on the agreement between parties where the transaction occurs. There are numerous nodes of such continuous blockchains on the blockchain network. It operates as a decentralized ledger. Whenever a new block is created, the transaction receives a digital signature fingerprint that cannot be changed and is comprised of hashtag functions from the preceding block with a unique output. When the outcome is altered without being checked, the transaction holds no validity and becomes unverified. This implies that all network nodes must get the same result when executing the hash. The transaction is validated if the modification passes this test.
The primary characteristics of blockchains are security, unchangeable records, and verification. The various blocks are linked by linking hashtags, and each block contains the hash code of the previous block, which is derived from the values produced when the new alliance comes up.
Each transaction that is initiated requires the connected nodes to validate the following;
- The history of the transaction is irrelevant. Also, the balance of the sender’s wallet address is verified.
- The recipient’s address is also validated.
If all of these criteria are fulfilled, the request is granted. The demand and the transaction’s private keys combine to create a digital authentication signature. Next, all this is transmitted and confirmed across all network nodes for key and signature matching using an output complicated hashing algorithm. Nodes fight with one another to solve the hash, guaranteeing the blockchain verification process twice.
The nodes are linked and are tiny high-end setups that can answer the code mentioned above for the correct result. They also broadcast the outcome to the network’s other transacting miner nodes to verify that the solution is right. This guarantees that all nodes continuously monitor the transactions and that they are publicly validated.
It should be kept in mind that a block may include a large number of transactions. Only the transacting node that verifies the transaction gets paid miners, establishing a fool-proof blockchain verification mechanism with healthy mining completion. Any error in computation will invalidate the transaction propagated across all linked nodes. For example, mining rewards on the Bitcoin blockchain network are often Bitcoin or Ethereum. After all, nodes mine the information and get their reward, and a transaction becomes confirmed, validated, and finished.
To Achieve Blockchain Verification, the Following Steps are Involved:
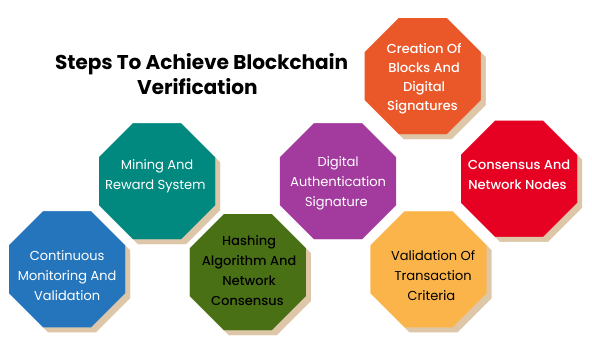
1. Creation of Blocks and Digital Signatures:
Blockchains consist of blocks of code linked together and rely on the parties’ agreement in a transaction. Each new block created in the blockchain receives a unique digital signature fingerprint that cannot be altered. This digital signature is generated using hash functions from the previous block, ensuring a chain of interconnected blocks.
- Blocks are created by bundling multiple transactions to form a single data unit.
- The transactions within a block are combined and processed using cryptographic hash functions.
- Hash functions generate a fixed-length alphanumeric string (hash) that uniquely represents the block’s data.
- Each block’s hash includes the previous block’s hash, creating a chain-like structure that ensures the integrity and immutability of the blockchain Technology.
- Digital signatures are cryptographic mechanisms that provide proof of authenticity and integrity for each transaction within a block.
- They are generated by encrypting the transaction data with the sender’s private key, ensuring that only the sender can create a valid signature.
2. Consensus and Network Nodes:
Blockchains operate as decentralized ledgers, meaning multiple nodes are distributed across the network. When a new block is created, it receives a digital signature. All network nodes must obtain the same result when executing the hash function for verification. This consensus ensures the integrity and validity of the transaction.
- Consensus mechanisms determine how nodes in the blockchain network agree on the state of the blockchain and validate transactions.
- In Proof of Work (PoW), miners compete to solve complex mathematical puzzles, requiring significant computational power.
- Once a miner finds a solution, it is verified by other nodes in the network before the block is added to the blockchain.
- Proof of Stake (PoS) allocates the right to create a new block based on the number of tokens a participant holds, promoting energy efficiency.
- Other consensus algorithms include Practical Byzantine Fault Tolerance (PBFT), Delegated Proof of Stake (DPoS), and more.
- Network nodes participate in the consensus process by verifying transactions, maintaining a copy of the blockchain, and reaching an agreement on the validity of new blocks.
In a PoW-based blockchain, miners compete to solve a complex mathematical problem, with the first miner to find a solution broadcasting it to the network. Once the key is verified, the block is added to the blockchain, and the miner receives a reward. This consensus mechanism ensures that all nodes in the network can independently verify and agree on the validity of transactions.
3. Validation of Transaction Criteria:
Connected nodes in the blockchain network validate specific criteria for each initiated transaction. These criteria include:
- Verification of the Sender’s Wallet Address: The sender’s wallet address balance is checked to ensure they have sufficient funds for the transaction.
- Validation of the Recipient’s Address: The recipient’s address is verified to ensure it is a valid and existing address within the blockchain network.
If all the criteria are met precisely, the transaction request is granted.
Specific criteria must be validated to ensure the integrity and validity of transactions. This includes verifying the sender’s wallet address and checking the balance to ensure they have sufficient funds for the transaction. Additionally, the recipient’s address is validated to ensure it is valid and exists within the blockchain network. These validation checks help prevent double-spending and ensure that only legitimate transactions are added to the blockchain.
- Certain criteria are validated before they are added to the blockchain to ensure the integrity of transactions.
- The sender’s wallet address is verified to ensure it is legitimate within the blockchain network.
- The balance of the sender’s wallet address is checked to ensure sufficient funds for the transaction.
- The recipient’s address is validated to ensure it is valid within the blockchain network.
- Other criteria, such as transaction timestamps or additional transaction-specific requirements, may be validated depending on the blockchain’s design.
4. Digital Authentication Signature:
A digital authentication signature is generated by combining the transaction request and unique private keys to enhance security further. This signature serves as proof of authenticity and integrity for the transaction. Digital authentication signatures prove a transaction is genuine and has not been tampered with. They are generated by combining the transaction data with the sender’s private key and applying cryptographic algorithms. The resulting signature serves as a unique identifier for the transaction and can be used to verify its authenticity.
- Digital authentication signatures provide a way to prove the authenticity and integrity of a transaction.
- Cryptography algorithms create them by combining the transaction data with the sender’s private key.
- The resulting signature is unique to the transaction and can be used to verify that the transaction has not been tampered with.
- Verifying the signature requires the transaction data, the sender’s public key, and the signature itself.
- Digital signatures ensure that transactions cannot be altered or forged without detection.
5. Hashing Algorithm and Network Consensus:
The digital authentication signature and the transaction request are transmitted and confirmed across all network nodes. A complex hashing algorithm, generated with the request and a nonce, is used for key and signature matching. Nodes within the network compete with each other to solve the hash function, ensuring the verification process is performed twice. Hashing algorithms play a crucial role in blockchain verification. They convert transaction data into fixed-size strings of characters, commonly referred to as hashes. Any slight change in the transaction data will result in a completely different hash. This property ensures the immutability of transactions and allows for easy integrity verification.
Network consensus is achieved by ensuring that all nodes in the network agree on the validity of transactions. In the case of PoW, nodes compete to solve a hash function associated with a block, and the first one to find a solution broadcasts it to the network. Other nodes then verify the resolution, and once consensus is reached, the block is added to the blockchain.
- Hashing algorithms convert transaction data into fixed-length alphanumeric strings called hashes.
- Commonly used hashing algorithms include SHA-256 (used in Bitcoin) and Keccak-256 (used in Ethereum).
- Hash functions have the property that even a small change in the input data will result in a significantly different output hash.
- This property ensures the integrity and immutability of transactions because any modification to a transaction would change its hash and break the chain of blocks.
- Network consensus is achieved by agreeing on the valid block through various mechanisms such as PoW, PoS, or other consensus algorithms.
- Consensus algorithms ensure that all network nodes agree on the order of transactions and prevent double-spending or other malicious activities.
6. Mining and Reward System:
In many blockchain networks, miners play a crucial role in verifying transactions. When a block contains multiple transactions, only the miner who successfully verifies the transaction within the block receives the mining reward. This reward can be in Bitcoin, Ethereum, or other cryptocurrencies. Mining helps maintain the integrity of the blockchain by incentivizing miners to validate transactions accurately.
Mining is the process of verifying and adding new blocks to the blockchain. Miners use computational power to solve complex mathematical problems, which requires significant computational resources and energy. The mining process verifies transactions and provides security to the blockchain by making it computationally expensive to alter past transactions.
Miners are incentivized to participate in the verification process through mining rewards. These rewards can include newly minted coins, transaction fees, or a combination. By offering tips, the blockchain network encourages miners to dedicate their resources to secure and validate transactions, ensuring the system’s overall integrity.
7. Continuous Monitoring and Validation:
Network nodes, typically high-end setups, continuously monitor and validate transactions. They broadcast the verified outcomes to other miner nodes in the network to ensure consensus and validation across all connected nodes. Any computational errors would invalidate the transaction and propagate the invalidity to all linked nodes.
In conclusion, achieving blockchain verification involves the interplay of digital signatures, consensus mechanisms, validation criteria, complex hashing algorithms, and mining rewards. This process ensures the security, immutability, and transparency of transactions within the blockchain network.
How are Blockchain Transactions Validated?
A Blockchain Validator is someone in charge of validating transactions on a blockchain. Every participant may become a blockchain validator by operating a full node on the Bitcoin Blockchain. However, the main reason to perform a complete node is to improve security. Unfortunately, this is an intangible incentive, so persuading someone to operate an entire node is insufficient. As a result, Blockchain Validators are mostly miners and mining pools that work complete nodes.
Differentiating Between Blockchain Validation and Blockchain Consensus
Understanding that “validation” and “consensus” are not synonymous is critical. A Blockchain Validator validates transactions by ensuring they are lawful (not malicious, double-spends, etc.).
On the other hand, the consensus defines the ordering of events on the blockchain — and reaches an agreement on that order.
Consensus essentially entails agreeing on the sequence of verified transactions. The validation comes before the consensus.
Related: Blockchain Use Cases
How are Blockchain Transactions Validated?
Whenever a transaction takes place, it is broadcast to the whole network. Miners take several transactions, verify “genuine,” and place them into a block after hearing the broadcasts.
However, miners “hear” various transactions at different times (due to latency issues, etc.). Furthermore, they may choose various transactions to put in their block depending on transaction costs. As a result, each miner is constructing their block. As a result, his block may be entirely different from the rest of the network’s miners.
Isn’t it true that everyone is constructing with various blocks? Then how are we going to agree on a single shared ledger!?”
That’s one of the protocol’s most appealing features. Miners are not required to construct the same global block. They may each create their partnership and reach a “consensus” on which block will be added next.
A miner may have a block that contains all legitimate transactions, yet his block may still need to reach a network agreement. If another person is chosen, he will build a new league and try again.
Methods for Determining Mining Reward: PoW and PoS
Mining may be very lucrative. That is why a blockchain network has more than one miner. Rather, many miners compete for the mining prize. As a result, blockchain networks must include a consensus mechanism that determines which miner will get the reward. Many approaches may be taken:
-
Proof-of-Work
The PoW reward mechanism is widely utilized in Bitcoin networks. Furthermore, poW is used by both the Bitcoin and Ethereum networks. When a new block is required, all miners on the network begin working on the hash problem. The mining reward is given to the miner who solves it first. It’s as easy as first come, first served.
-
Proof-of-Stake
PoS and PoW have the same goal: to validate transactions by generating a new hash. In a PoS system, however, nodes are not vying for the mining reward. Instead, just one node is chosen to verify the next hash. The richness of the node – or, in other words, its stake in the network – is the selection criterion. As a result, since only one node is engaged in solving the mathematical issue in a PoS-based network, energy usage will be considerably lower.
Furthermore, the incentive in a PoS system needs to be paid in freshly created currencies. Instead, the chosen node will be paid a transaction charge. When the network is established, all coins are already issued. As a result, nodes that discover a new hash in a PoS system are referred to as “forgers” rather than “miners.”
There are other methods for validating transactions, such as Proof-of-Authority, Proof-of-Burn, Proof-of-Capacity, and Proof-of-Elapsed Time. In theory, all of these systems have the same goal: to validate new data on the network. Only how the miners are chosen will vary.
Conclusion
As you can see, consensus techniques mainly concern consensus on sequencing events/transactions (and who gets to add them). The miner validates the transactions before they are included in the block. When a block winner is chosen, the remainder of the Blockchain Validators votes again. The miners create the league, while the Blockchain Validators ensure it is legitimate. If consensus is achieved, the network may proceed to the next block.
In addition to understanding the blockchain verification process, it’s worth mentioning that some companies, like SoluLab, offer comprehensive services in blockchain technology. SoluLab is a leading blockchain development company that creates blockchain solutions for various industries.
Their team of top-skilled blockchain developers can assist businesses in leveraging the benefits of blockchain technology by developing custom blockchain applications tailored to specific needs. Whether creating decentralized applications (DApps), implementing smart contracts, or building private or public blockchains, SoluLab has the expertise to deliver cutting-edge solutions.
Additionally, SoluLab provides blockchain consulting services, where their experts work closely with clients to analyze their business requirements and identify the most suitable blockchain solutions. Through consulting, businesses can gain insights into the potential applications of blockchain technology and devise strategies for its successful implementation. Contact SoluLab to get a free consultation now!
FAQs
1. What is blockchain verification?
Blockchain verification is validating and confirming transactions on a blockchain network. It involves verifying the sender’s wallet balance and the recipient’s address and ensuring the transaction is secure and tamper-proof. Through consensus algorithms and cryptographic techniques, blockchain verification ensures the integrity and immutability of the transactions.
2. How does blockchain verification ensure security?
Blockchain verification achieves security through decentralization and cryptographic techniques. The distributed nature of blockchain networks ensures that transactions are validated by multiple nodes, making it difficult for malicious actors to tamper with the data. Additionally, cryptographic algorithms provide digital signatures and hash functions that secure the authenticity and integrity of the transactions.
3. Why is blockchain verification considered trustworthy?
Blockchain verification is considered trustworthy because it operates on a decentralized network of nodes that collectively validate and verify transactions. The consensus mechanism ensures that all nodes agree on the validity of transactions, eliminating the need for intermediaries and making it difficult for fraudulent activities to go unnoticed. The transparency of blockchain also allows participants to audit and verify transactions independently.
4. Can blockchain verification be tampered with?
Blockchain verification is designed to be tamper-proof. Once a transaction is verified and added to a block, it becomes virtually immutable due to the cryptographic link with previous blocks. Altering a transaction’s data would require modifying subsequent blocks, which is computationally infeasible and highly improbable due to the consensus mechanism and the network’s distributed nature.
5. How long does blockchain verification take?
The time taken for blockchain verification depends on various factors, including the specific blockchain protocol, network congestion, and the complexity of the transaction. In general, blockchain networks aim to achieve fast and efficient verification. For example, Bitcoin aims to confirm transactions within an average of 10 minutes, while other top blockchain platforms may have different verification times based on their consensus algorithms and network conditions.







