
Cryptocurrencies have witnessed an explosive global surge in popularity, attracting over 300 million users in nearly 150 countries. The rapid adoption can be attributed to their convenience compared to traditional banks, cost-saving benefits by avoiding transaction fees, and accessibility for prospective investors.
However, like any financial system, cryptocurrencies are not without their imperfections. There exist security threats within the cryptocurrency realm that pose risks when dealing with digital assets. This cryptocurrency security blog serves as a valuable resource to enhance your safety in the crypto space. We’ve delved into crypto wallet security, prevalent crypto scams, and the pros and cons of digital currencies, and outlined essential security measures to safeguard your cryptocurrency wallets.
So, let’s dive in!
What Exactly is a Cryptocurrency?
Cryptocurrency is a form of digital currency that employs advanced encryption techniques, making it extremely difficult to counterfeit. Unlike conventional currencies, cryptocurrencies operate on a blockchain, which can be thought of as a virtual ledger that operates independently, beyond the control of governments and traditional banks.
Starting with the emergence of Bitcoin (BTC) in 2009, the term “cryptocurrency” stems from its utilization of encryption for transaction verification. Since then, the world has witnessed the ascent of other cryptocurrencies like Ether (ETH), Binance Coin (BNB), Tether (USDT), and many more, igniting heightened interest in these novel digital assets.
Read Our Blog Also: Top 10 Decentralized Crypto Exchanges to Consider
Cryptocurrency Theft Is Almost Always Avoidable
Cryptocurrency wallet thefts can usually be avoided through proactive measures and cautious practices. Investors in cryptocurrencies have the means to protect themselves from frequent security breaches. By implementing specific security protocols and exercising vigilance to steer clear of risky situations, they can participate in one of the world’s most rapidly expanding industries without the constant fear of losing their hard-earned digital assets.
While cybercriminals continually seek opportunities to exploit weaknesses, many times, it’s the straightforward actions that hold the most significance for the typical investor. These actions encompass securing their cryptocurrencies in a personal and highly secure wallet and, importantly, refraining from connecting their wallets to precarious platforms.
9 Cryptocurrency Security Measures You Should Know About!
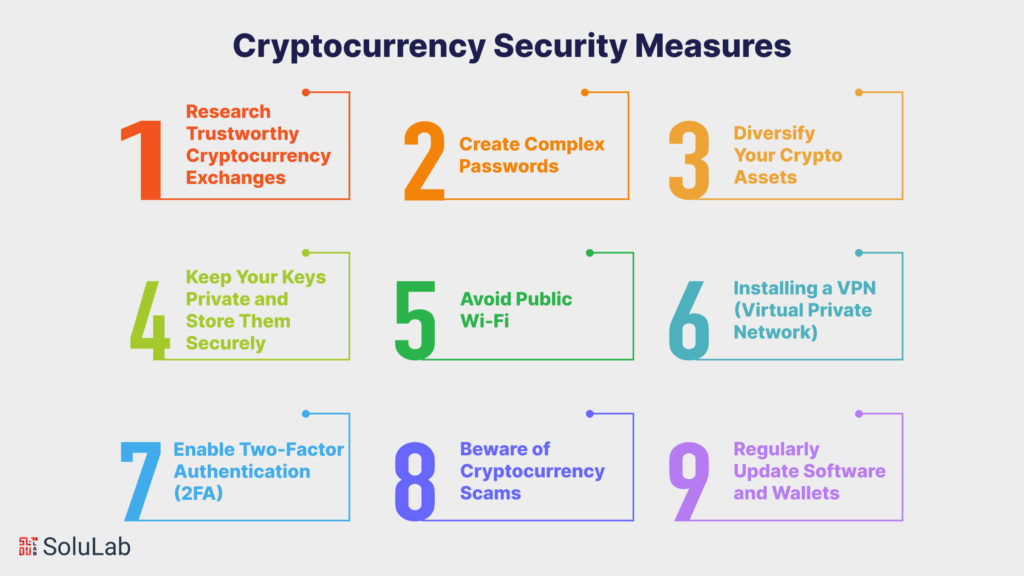
Consider using these cryptocurrency security procedures to help keep your crypto wallets safe from various sorts of hackers.
Research Trustworthy Cryptocurrency Exchanges
When selecting a cryptocurrency exchange, research is your best defense against potential risks. Here’s what you should do:
- Start by checking the exchange’s reputation.
- Look for user reviews, testimonials, and feedback on social media and forums. Investigate whether the exchange complies with relevant regulations in your country or region, as regulatory oversight can enhance security.
- Additionally, assess the exchange’s security measures.
- Reputable exchanges employ cold storage solutions to keep most user funds offline, safeguarding them from online threats. They also do frequent security audits in order to detect vulnerabilities.
- Moreover, inquire if the exchange offers insurance coverage for digital assets in case of theft or hacking incidents.
Be cautious of new or unregulated exchanges, as they may lack a proven track record of security. Remember that the security of your investments largely depends on the exchange you choose, so take the time to make an informed decision.
Create Complex Passwords
Passwords are your first line of defense in protecting your cryptographic operations. Follow these steps to generate a strong password:
- Uppercase and lowercase letters, numerals, and special characters should all be combined.
- Avoid easily guessable information like names, birthdays, or common phrases.
- Make your passwords lengthy and unique for each online account.
- To develop and securely store complicated passwords, consider utilizing a trustworthy open-source password manager.
Frequent password changes are also recommended and never use the same password across multiple accounts. Adhering to these practices can significantly reduce the risk of unauthorized access to your cryptocurrency accounts.
Read Also: The Ultimate Guide for Asset Tokenization on Blockchain
Diversify Your Crypto Assets
Diversification is a risk management approach that spreads your assets among other cryptocurrencies. This approach aims to reduce the impact of a poor-performing asset on your overall portfolio. Here’s how it works:
- Invest in a mix of well-established cryptocurrencies like Bitcoin (BTC) and Ethereum (ETH), along with promising but less-known projects.
- Divide your assets according to your risk level and long-term goals.
- Regularly review your portfolio and make adjustments as appropriate.
Diversifying your crypto assets can help you mitigate the inherent volatility of the cryptocurrency market and minimize potential losses.
Keep Your Keys Private and Store Them Securely
Your keyphrase, also known as your private key or recovery phrase, is the ultimate access to your cryptocurrency wallet development. Guarding it is paramount. Follow these key security practices:
- Never share your key phrase with anyone. It should remain confidential.
- Store your keyphrase offline in a secure location, such as a physical safe or a hidden, tamper-proof container.
- Consider using hardware wallets or paper wallets, both of which keep your keyphrase offline and out of reach of online threats.
- Avoid storing digital copies of your keyphrase on cloud services, email accounts, or unsecured devices.
Losing your keyphrase can result in permanent loss of access to your cryptocurrency holdings, so take utmost care in safeguarding it.
Avoid Public Wi-Fi
Public Wi-Fi networks are notorious for their lack of security, making them vulnerable to hackers who can intercept your online activities. To protect your cryptocurrency holdings:
- Refrain from accessing your crypto accounts or making transactions while connected to public Wi-Fi.
- If you need to access your crypto holdings on the go, consider using your mobile data connection or setting up a personal hotspot for a secure internet connection.
- Use a VPN (Virtual Private Network) when connecting to public Wi-Fi networks to encrypt your online traffic and enhance your privacy.
By avoiding public Wi-Fi, you reduce the risk of unauthorized access to your cryptocurrency accounts and transactions.
Check Out Our Blog: Binance Business Model and Revenue Sources Explained
Installing a VPN (Virtual Private Network)
A VPN is a potent tool for bolstering your online security and privacy, particularly when engaging with cryptocurrencies. Here’s a thorough summary of its features:
- A VPN employs advanced encryption techniques to secure your internet connection. This encryption makes it exceptionally challenging for malicious actors to intercept or decipher your data.
- By using a VPN, you obscure your real IP address with that of the VPN server you connect to. This not only enhances your privacy but also adds an extra layer of anonymity, making it difficult for prying eyes to trace your online actions back to you.
- VPNs enable you to choose servers in different locations worldwide. This feature is invaluable when dealing with cryptocurrency services that may have geographical restrictions.
- When selecting a VPN provider, opt for a reputable one that offers robust encryption and a no-logs policy. Using a VPN while managing your cryptocurrencies can protect your transactions and communications from potential threats.
Enable Two-Factor Authentication (2FA)
Two-factor authentication (2FA) adds an extra layer of security to your cryptocurrency accounts by requiring two forms of verification to access them. Here’s how to set up and use 2FA effectively:
- Enable 2FA on all your cryptocurrency exchange accounts and wallets that offer this feature. Typically, 2FA involves receiving a one-time code on your mobile device or a hardware token, which you must enter along with your password.
- Ensure that your 2FA method is secure and not easily accessible to others. With 2FA in place, even if someone manages to obtain your password, they won’t be able to access your accounts without the secondary verification code.
- This security feature uses cryptographic keys and time-sensitive codes to validate your identity, adding an extra layer of protection to your cryptocurrency holdings.
Beware of Cryptocurrency Scams
Cryptocurrency scams come in various forms, and recognizing them is crucial to safeguarding your investments. Common types of scams include:
- Phishing Scams: Scammers send deceptive emails or messages that appear legitimate, enticing you to click on links that lead to fake websites designed to steal your login information.
- Ponzi Schemes: Fraudulent investment schemes promise unrealistically high returns and rely on funds from new investors to pay previous ones.
- Impersonation Scams: Scammers impersonate influential figures or projects in the crypto space, asking for contributions or investments.
To avoid falling victim to scams:
- Verify the legitimacy of investment opportunities and double-check URLs and sender email addresses.
- Be skeptical of unsolicited offers and deals that seem too good to be true.
- Seek advice from trusted sources within the crypto community when in doubt.
Read Also: What are the Benefits of Using Digital Identity with Blockchain in the Future?
Regularly Update Software and Wallets
Keeping your software and wallets up to date is essential for maintaining security. Developers continually release updates to address vulnerabilities and enhance security features. Here’s why you should prioritize updates:
- Security patches: Updates often include patches to fix known vulnerabilities, reducing the risk of exploitation.
- Improved features: Updates may introduce additional security layers or user-friendly security settings.
- Compatibility: Ensuring your software is up to date helps it work seamlessly with the latest security protocols.
Emerging Technologies in Enhancing Security in Cryptocurrency Wallets

Emergent technologies are continually playing a significant role in enhancing the security of cryptocurrency wallets. These advancements aim to protect users from various threats and vulnerabilities. Here are some emerging technologies and trends in cryptocurrency wallet security:
Read Our Blog: 8 Best NFT Wallets
-
Multi-Signature Wallets (Multisig)
Multisig wallets require multiple cryptographic signatures to authorize a transaction, typically involving several private keys held by different parties. This approach adds an extra layer of security by preventing a single point of failure.
-
Hardware Security Modules (HSMs)
HSMs are specialized hardware devices designed to secure and manage cryptographic keys. They are becoming increasingly popular for securing private keys in both hot and cold wallets. HSMs provide tamper-resistant protection for keys and cryptographic operations.
-
Biometric Authentication
Biometric authentication methods, such as fingerprint recognition, facial recognition, and iris scanning, are being integrated into cryptocurrency wallets for secure user authentication. These methods enhance the security of accessing wallets on mobile devices.
Know more: Blockchain Verification Process: Explained
-
Quantum-Resistant Cryptography
With the rise of quantum computing, which poses a potential threat to existing cryptographic algorithms, quantum-resistant cryptography is gaining importance. Wallets are exploring post-quantum cryptographic techniques to safeguard against future quantum attacks.
-
Zero-Knowledge Proofs (ZKPs)
ZKPs enable the verification of data without revealing the data itself. This technology is used in privacy-focused cryptocurrencies and wallets to enhance transaction privacy while maintaining security.
-
Secure Enclaves and Trusted Execution Environments (TEEs)
Secure enclaves, like Intel’s SGX and ARM TrustZone, provide isolated execution environments within a device’s CPU. They are used to store and protect cryptographic keys, ensuring that even if the device is compromised, the keys remain secure.
-
Decentralized Identity and Self-Sovereign Identity (SSI)
These emerging concepts empower users to have full control over their digital identities and the associated cryptographic keys. SSI technologies aim to reduce reliance on centralized identity providers, enhancing user privacy and security.
-
Blockchain-Based Authentication
Some wallets are exploring blockchain-based authentication methods, where a user’s identity is linked to their wallet address on a blockchain. This reduces the risk of phishing attacks and unauthorized access.
-
AI-Powered Threat Detection
Artificial intelligence and machine learning are being employed to detect suspicious activities and potential threats in cryptocurrency wallets. These technologies can identify anomalies and alert users to unusual behavior.
-
Biometric Multisig
Combining biometric authentication with multisig wallets adds an extra layer of security. Users can authorize transactions with their biometric data, making it difficult for malicious actors to compromise wallets.
-
Recovery Protocols
Emerging wallet recovery protocols, such as social recovery or threshold schemes, allow users to regain access to their wallets in case of loss or theft. These methods involve trusted contacts or multiple key holders.
-
Delegated Proof of Stake (DPoS) and Consensus Mechanisms+
DPoS and alternative consensus mechanisms are designed to improve blockchain network security, which indirectly enhances the security of wallets operating on these networks.
Final Words
In conclusion, the world of cryptocurrency offers immense potential, but it also presents unique challenges, particularly in the realm of security. As evidenced by recent statistics, the threat of cyberattacks and scams targeting cryptocurrency holders remains ever-present. However, armed with knowledge and adopting best practices, investors can navigate this landscape with confidence.
Implementing robust security measures, such as choosing reputable exchanges, creating strong passwords, enabling two-factor authentication, safeguarding private keys, and staying vigilant against scams, can significantly mitigate risks. Furthermore, emerging technologies like multi-signature wallets, hardware security modules, biometric authentication, and quantum-resistant cryptography are paving the way for enhanced wallet security.
As the cryptocurrency ecosystem evolves, the collective efforts of users, developers, and security experts continue to fortify the foundations of a more secure and prosperous digital financial future. By adhering to these best practices and staying informed about the latest security trends, cryptocurrency enthusiasts can enjoy the benefits of this transformative technology while safeguarding their digital assets from potential threats.
SoluLab, one of the leading cryptocurrency companies, stands as a trusted partner in the ever-evolving world of cryptocurrency, offering cryptocurrency wallet development services that are second to none. With an unwavering commitment to ensuring the best cryptocurrency key security, SoluLab specializes in crafting robust and secure cryptocurrency wallet applications. Our expert team combines cutting-edge technology with a deep understanding of the intricate nuances of cryptocurrency to deliver tailor-made solutions that meet the highest standards of security and user experience. Whether you are looking for a new cryptocurrency wallet app development from the ground up or enhancing the security of an existing one, SoluLab’s expertise and dedication are your keys to success in the cryptocurrency arena. Contact SoluLab today to embark on your cryptocurrency journey with confidence.
FAQs
1. What is a cryptocurrency wallet, and why is security crucial for it?
A cryptocurrency wallet is a digital tool that allows users to store, send, and receive cryptocurrencies. Security is paramount for cryptocurrency wallets because they hold valuable digital assets. Without proper security, users risk losing their funds to hackers or scams.
2. What types of cryptocurrency wallets are there, and which one is the most secure?
There are various types of cryptocurrency wallets, including hardware wallets, software wallets, paper wallets, and mobile wallets. Among these, hardware wallets are generally considered the most secure as they store private keys offline, making them immune to online threats.
3. What are the key security measures I should take to protect my cryptocurrency wallet?
Essential security measures include using strong and unique passwords, enabling two-factor authentication (2FA), keeping private keys offline, avoiding public Wi-Fi for wallet access, and staying vigilant against phishing scams.
4. What emerging technologies are shaping the future of cryptocurrency wallet security?
Emerging technologies like multi-signature wallets, hardware security modules (HSMs), biometric authentication, quantum-resistant cryptography, and secure enclaves are advancing wallet security, making it more robust and resilient against evolving threats.
5. Is diversifying my crypto assets a security measure?
Yes, diversifying your cryptocurrency holdings across different assets can be a security measure. It helps mitigate risk by reducing the impact of poor-performing assets and adds a layer of protection against market volatility.
6. How can SoluLab help enhance the security of my cryptocurrency wallet?
SoluLab specializes in cryptocurrency wallet development services and cryptocurrency wallet app development. We can create highly secure and user-friendly wallet solutions tailored to your needs, ensuring the best cryptocurrency key security.






