In the rapidly evolving landscape of technology, few innovations have captured the world’s attention and potential as profoundly as blockchain. This revolutionary technology has disrupted traditional models of trust, offering decentralized and tamper-proof solutions that span across industries. As blockchain applications become increasingly integrated into everyday processes, ensuring their security has become paramount. Developers, as the architects of these innovative solutions, bear the responsibility of safeguarding the integrity and resilience of blockchain networks.
Blockchain’s foundation in cryptographic principles and decentralized consensus mechanisms is inherently secure, but like any technology, it is not impervious to threats. The distributed and immutable nature of blockchain introduces unique challenges that require a deep understanding of its security landscape. This blog aims to provide developers, whether newcomers to the blockchain space or seasoned experts, with a comprehensive guide to the best practices that form the bedrock of blockchain security.
From the fundamental concepts of blockchain security to practical techniques for fortifying smart contracts and networks, this blog will delve into the multifaceted aspects of blockchain security. By grasping these principles and integrating them into their development workflows, developers can bolster their ability to architect blockchain solutions that not only harness the technology’s transformative potential but also stand resilient against a range of security risks.
Read Also: How Does the Blockchain Work?
In the sections that follow, we will explore key practices that encompass everything from secure development methodologies and cryptographic protocols to auditing processes and monitoring strategies. Whether you’re embarking on your first blockchain project or seeking to enhance the security of existing applications, the insights within this blog will empower you to navigate the intricate landscape of blockchain security with confidence.
Understanding the basics of Blockchain Security
Blockchain technology has brought about a paradigm shift in how we handle data, transactions, and trust in the digital realm. At its core, a blockchain is a decentralized and immutable digital ledger that records transactions in a secure and transparent manner. However, despite its inherent security features, developers must still be well-versed in the fundamental principles of blockchain security to build applications that withstand potential threats. Let’s delve into the basics of blockchain security and explore the key concepts every developer should understand.
Decentralization and Consensus Mechanisms:
One of the foundational pillars of blockchain security is decentralization. Unlike traditional centralized systems where a single entity controls the entire network, blockchain operates on a decentralized network of nodes, ensuring that no single point of failure exists. This distribution of power prevents malicious actors from easily manipulating the system.
To maintain consensus in a decentralized network, various consensus mechanisms are employed. The most common is Proof of Work (PoW), where nodes (often referred to as miners) compete to solve complex mathematical puzzles to validate transactions and add new blocks to the chain. This mechanism ensures that the majority of network participants agree on the state of the blockchain. Another mechanism, Proof of Stake (PoS), relies on validators who are chosen to create new blocks based on the amount of cryptocurrency they “stake” as collateral. Both PoW and PoS enhance the security of the blockchain by requiring significant computational resources or economic incentives to compromise the system.
Read Our Blog: Building Trust in a Digital World: The Power of Blockchain Development
Cryptographic Hash Functions:
Cryptographic hash functions are the building blocks of blockchain security. They take an input (data) and produce a fixed-size output (hash) that is unique to the input. A small change in the input will result in a completely different hash, making it virtually impossible to reverse-engineer the original data. This property ensures the immutability of the blockchain.
Hash functions are used to secure transactions and create the linkage between blocks in the chain. Each block contains a reference to the hash of the previous block, creating a cryptographic “chain” that is resistant to tampering. Any alteration to a block’s data would require changing the hash of not only that block but all subsequent blocks, which is practically unfeasible in a decentralized network.
Public and Private Key Cryptography:
Public and private key cryptography underpins the security of blockchain transactions. Each participant in the network possesses a pair of cryptographic keys: a public key and a private key. The public key, which is derived from the private key, serves as an address that can receive funds. The private key, held only by the owner, is used to sign transactions and prove ownership.
When someone initiates a transaction, they sign it with their private key. Other participants can use the sender’s public key to verify the signature and ensure the transaction’s authenticity. This cryptographic mechanism guarantees the integrity of transactions and prevents unauthorized access.
Read Also: Blockchain Verification Process: Explained
Smart Contracts and Vulnerabilities:
Smart contracts, self-executing code deployed on the blockchain, are a powerful feature of blockchain technology. However, they also introduce their own security considerations. Vulnerabilities such as reentrancy attacks, integer overflow, and unauthorized access to functions can lead to serious security breaches.
Developers must rigorously audit and test their smart contracts to identify and mitigate vulnerabilities. Code reviews, static analysis tools, and external audits are essential steps in ensuring the security of smart contracts before deployment.
Why are blockchain security practices important?
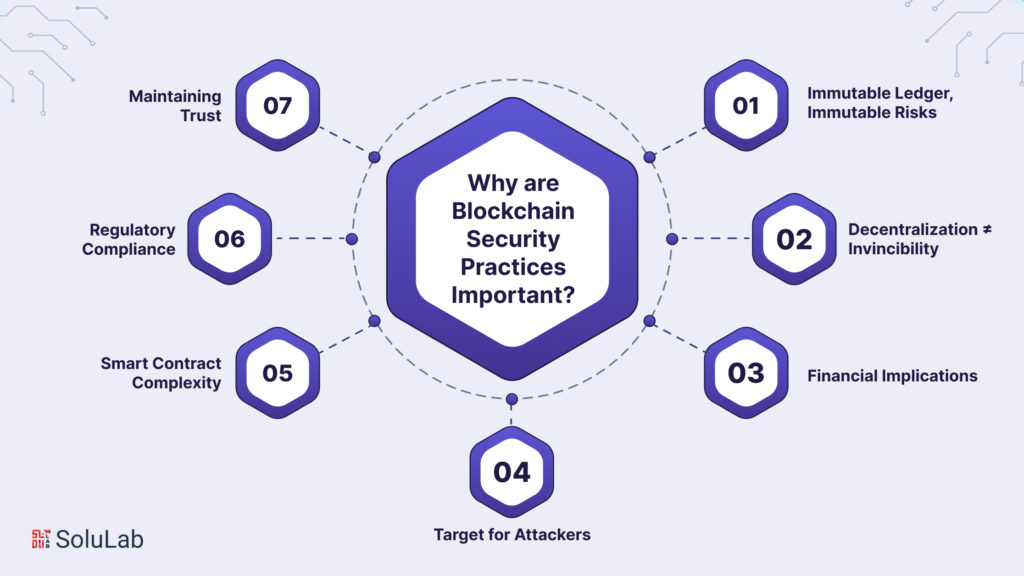
Blockchain technology has garnered significant attention for its potential to revolutionize industries, but its adoption also brings forth a critical responsibility: ensuring robust security practices. While blockchain offers inherent security features due to its decentralized and immutable nature, developers must implement a comprehensive set of security practices to fortify the technology against evolving threats. Let’s explore why blockchain security practices are of paramount importance in the modern digital landscape.
Read Our Blog: Why You Need To Leverage Blockchain For Your Business Today?
-
Immutable Ledger, Immutable Risks:
The immutability of blockchain, often touted as a core strength, presents a double-edged sword. Once data is recorded on the blockchain, it cannot be altered. While this is advantageous for maintaining data integrity, it also means that any vulnerabilities or breaches can have far-reaching and irreparable consequences. Proper security measures are crucial to prevent malicious actors from exploiting vulnerabilities and introducing unauthorized changes to the blockchain.
-
Decentralization ≠ Invincibility:
Decentralization is a key feature that sets blockchain apart from traditional centralized systems. However, it does not guarantee invincibility against security threats. While decentralization minimizes the risk of a single point of failure, it does not eliminate the possibility of attacks or vulnerabilities. Developing secure applications in a decentralized environment demands a different set of strategies and practices.
-
Financial Implications:
Many blockchain applications involve the management of valuable assets, whether they are cryptocurrencies, digital assets, or sensitive information. A breach in the security of a blockchain application can result in financial losses, reputation damage, and legal consequences. The potential impact of a security breach amplifies the need for developers to prioritize robust security practices.
-
The target for Attackers:
The distributed nature of blockchain networks makes them attractive targets for attackers seeking to exploit vulnerabilities. From DDoS attacks to 51% attacks (where an attacker gains control of the majority of mining power in PoW networks), malicious actors can disrupt operations, manipulate data, and even double-spend cryptocurrencies. Implementing security measures is essential to thwart these attacks and maintain the integrity of the network.
-
Smart Contract Complexity:
Smart contracts, while powerful, introduce complexity that can lead to unforeseen vulnerabilities. The infamous “DAO hack” in Ethereum, where an attacker exploited a vulnerability in a smart contract to drain funds, serves as a stark reminder of the risks associated with smart contract development. Security practices such as code audits, testing, and formal verification are crucial to prevent such incidents.
Read Our Blog Post: Top 10 Blockchain Development Companies in 2023
-
Regulatory Compliance:
As blockchain technology becomes more mainstream, regulatory requirements are becoming a significant consideration. Organizations that handle sensitive data or financial transactions on blockchain networks must adhere to relevant regulations. Proper security practices ensure compliance with data protection and financial regulations, avoiding legal and financial repercussions.
-
Maintaining Trust:
Blockchain’s promise of transparency and trust is only as strong as the security that underpins it. If security breaches become frequent, users and stakeholders may lose trust in the technology, hindering its adoption and potential. By implementing rigorous security practices, developers can help maintain the trust that is vital for the success of blockchain applications.
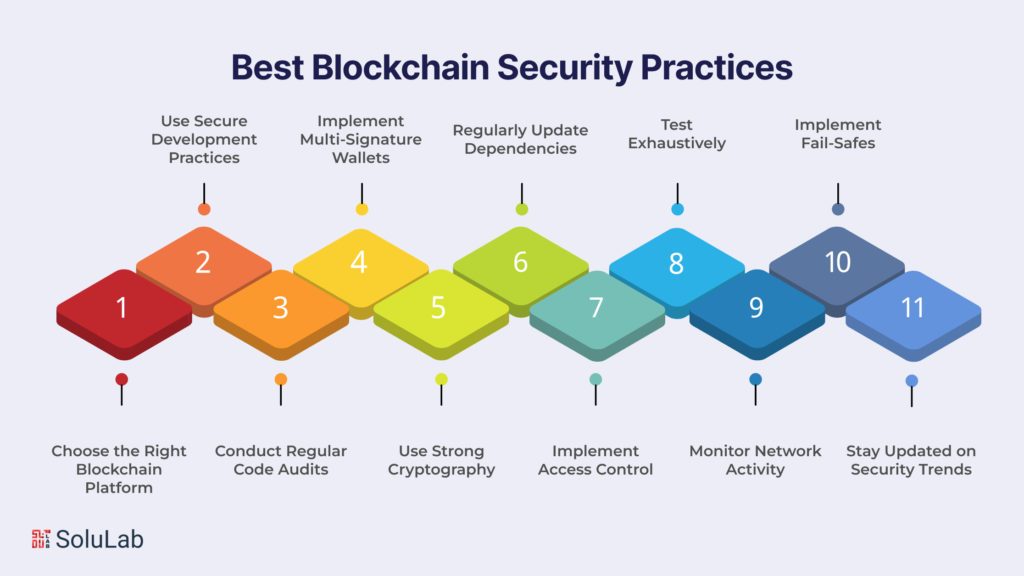
Best Blockchain Security Practices
Before delving into best practices, it’s crucial to have a solid understanding of blockchain security fundamentals. This includes comprehending the decentralized nature of blockchain networks, consensus mechanisms (such as Proof of Work and Proof of Stake), cryptographic hashing, public and private keys, and the concept of smart contracts. A strong grasp of these concepts will lay the foundation for effective security practices.
Read Also: What are the Benefits of Using Digital Identity with Blockchain in the Future?
Choose the Right Blockchain Platform
Selecting the appropriate platform for blockchain security for your project is the first step toward ensuring security. Different blockchain platforms offer varying levels of security, consensus mechanisms, and smart contract capabilities. Ethereum, for instance, is a popular choice for decentralized applications, but there are other options like Binance Smart Chain, Cardano, and more. Choose a platform that aligns with your project’s requirements and security considerations.
Use Secure Development Practices
Secure coding practices are the cornerstone of blockchain security. Just like in traditional software development, following coding standards, avoiding vulnerabilities, and adhering to best practices like the OWASP Top Ten for web application security is essential. Blockchain-specific vulnerabilities, such as reentrancy attacks and timestamp dependence, should also be thoroughly understood and guarded against.
Conduct Regular Code Audits
Regular code audits by experienced blockchain security professionals are essential to identify and mitigate potential vulnerabilities. These audits involve a comprehensive review of the smart contracts and other code components to uncover vulnerabilities, backdoors, and logic errors that could compromise security.
Implement Multi-Signature Wallets
Multi-signature wallets require multiple private keys to authorize transactions, adding an extra layer of security. This prevents a single point of failure and unauthorized access to funds. Implement multi-signature wallets for important transactions or fund storage.
Use Strong Cryptography
Cryptography is the bedrock of blockchain security. Utilize strong cryptographic algorithms for key generation, encryption, and hashing. Regularly update your cryptographic libraries and algorithms to protect against emerging threats.
Regularly Update Dependencies
Blockchain applications often rely on third-party libraries and dependencies. These libraries can have vulnerabilities that hackers may exploit. Keep all dependencies up to date and monitor security announcements to address vulnerabilities promptly.
Read Our Blog Post: What Are The Benefits of Hiring a Blockchain Developer?
Implement Access Control
Access control mechanisms are crucial for restricting unauthorized access to your blockchain application. Utilize role-based access control (RBAC) and permissions to ensure that only authorized parties can interact with sensitive functions.
Test Exhaustively
Thoroughly test your smart contracts and blockchain applications before deployment. Utilize techniques like unit testing, integration testing, and end-to-end testing to uncover bugs and vulnerabilities. Implement continuous integration and continuous deployment (CI/CD) pipelines to automate testing processes.
Monitor Network Activity
Implement robust monitoring tools to track network activity and transactions. This will help detect unusual patterns, potential attacks, and unauthorized activities. Implement alerts to notify the development team of suspicious behavior.
Implement Fail-Safes
Incorporate fail-safe mechanisms to mitigate the impact of potential breaches. These mechanisms could include emergency pause features, circuit breakers, or upgradeability mechanisms that allow you to fix vulnerabilities without compromising the entire system.
Stay Updated on Security Trends
Blockchain security is a constantly evolving field. Stay informed about the latest security trends, vulnerabilities, and best practices. Participate in forums, attend conferences, and follow industry experts to ensure you’re up to date with the latest security developments.
Conclusion
Blockchain technology holds immense promise for reshaping industries and enhancing security, but its potential can only be fully realized if security is prioritized throughout the development lifecycle. By adhering to these best practices, blockchain developers can create robust and secure applications that stand up to the evolving threat landscape. As the blockchain ecosystem continues to grow, a proactive approach to security is not just a choice – it’s an imperative.
From understanding the foundational concepts of decentralized networks and cryptographic principles to mastering the intricacies of smart contract vulnerabilities and monitoring strategies, these best practices serve as a comprehensive guide for developers at all stages of their blockchain journey. By adopting these practices, developers can rise to the challenge of not only crafting innovative solutions but also upholding the core tenets of security and trust that underpin the blockchain’s promise.
Read Also: Beginners’ Guide 101 to Outsourcing Blockchain Development
As technology continues to push the boundaries of what’s possible, the responsibility to protect and advance its potential falls squarely on the shoulders of developers. Secure coding practices, continuous audits, stringent testing, and staying attuned to emerging blockchain security solutions trends form a shield against threats that could undermine the very foundations of blockchain’s effectiveness. Furthermore, the importance of collaboration and knowledge-sharing among developers cannot be overstated, as a united effort is necessary to stay one step ahead of adversaries.
SoluLab is a leading blockchain development company that places the highest priority on blockchain security solutions. With a team of experts specializing in blockchain development services, they ensure the creation of cutting-edge applications that meet your unique needs.
From concept to deployment, their blockchain development solutions prioritize security at every step, safeguarding your data and transactions. Whether you require secure smart contracts or robust decentralized applications, their blockchain development services empower your business with the utmost security and efficiency. So, contact SoluLab now if you want to hire the best blockchain developers.
FAQs
1. Why is blockchain security so important for developers?
Blockchain security is of paramount importance because it ensures the integrity, trustworthiness, and functionality of blockchain applications. While blockchain offers inherent security features, it is not impervious to threats. Developers must implement best practices to safeguard against vulnerabilities, unauthorized access, and potential attacks that could compromise the entire system. Prioritizing security from the outset helps maintain user trust, prevents financial losses, and upholds the transformative potential of blockchain technology.
2. What are some common security vulnerabilities in blockchain applications?
Blockchain applications can be susceptible to various vulnerabilities, including smart contract flaws (reentrancy attacks, overflow vulnerabilities), insecure key management, insufficient validation of inputs, and susceptibility to distributed denial-of-service (DDoS) attacks. Addressing these vulnerabilities requires understanding blockchain-specific risks and implementing secure coding practices, regular audits, and continuous monitoring to mitigate potential threats.
3. How can developers ensure the security of smart contracts?
Developers can ensure the security of smart contracts by following a multi-faceted approach. First, conduct thorough code reviews and testing to identify vulnerabilities before deployment. Second, utilize static analysis tools to identify potential issues early in the development process. Third, consider external audits by security experts who specialize in blockchain to uncover hidden vulnerabilities. Finally, implement best practices such as limiting the use of external calls, using fail-safes like circuit breakers, and continuously updating smart contracts to address emerging threats.
4. What role does cryptography play in blockchain security?
Cryptography is a foundational element of blockchain security. It is used to secure transactions, create cryptographic hashes for data integrity, and manage public and private keys. Public key cryptography ensures that only authorized parties can sign transactions and access encrypted data. By leveraging strong cryptographic algorithms and keeping libraries up to date, developers can reinforce the confidentiality, authenticity, and non-repudiation aspects of blockchain transactions, contributing to a more secure ecosystem.